Data – security data specifically – is abundant and, when optimized, is capable of unlocking connected business insights for every user. As data initiatives become more important to security teams, how organizations leverage security telemetry can be critical to enabling high fidelity analysis, decisioning, response, and assurance outcomes. For a majority of analysts, navigating enterprise tools and extracting information relies on knowing their organization’s security data maturity. However, for most organizations, stages remain undefined, creating low stakeholder buy-in when trying to be strategic about how security data can be used.
What is a Security Data Maturity Model?
The Security Data Maturity Model (SDMM), developed by the cybersecurity team at Comcast, is a prescriptive, five stage approach to how organizations can use and leverage security data to make data-driven security decisions.
This conceptual framework provides strategic value to help organizations better asses their foundational underlying data infrastructure that is currently in place and shares steps and guidance based on level of security data processing and infrastructure maturity. The SDMM enables security and data teams to mature their security data estate and progress to an open architecture that fosters a critical assessment to understand what policies, procedures, and resources must be adopted to reduce the overall risk exposure.
How can organizations benefit from a Security Data Maturity Model?
There are many beneficial reasons for an organization to investigate and use a SDMM, including:
- Developing an overall security data strategy. The advent of big data, artificial intelligence and machine learning has highlighted that data is a core asset, and many organizations have a data strategy. But to have an enterprise-wide global data strategy, security data must be included. Moreover, to have meaningful security data, you must add data from outside the security realm to provide deeper context.
- Data can be used to make centralized, intelligent decisions. Higher levels of security data maturity lead to better organizational decision-making.
- With context, a SDMM can help provide deeper organizational insights. Enterprises can make better data-driven decisions based on the data’s context and by showing how the data relates to specific areas such as governance, compliance, and risk management.
- Help facilitate organizations moving from a reactive to a proactive state. SDMMs can facilitate moving an organization’s cultural state from one that is reactive to one that is more proactive and prescriptive. From a security standpoint, this means getting ahead of the bad guys and putting systems, resources, and processes in place to anticipate risks and breaches before they occur.
- Business goals alignment. A SDMM can help a decentralized enterprise align its security and business goals across business units.
- Cost savings. A SDMM can help save the organization money by focusing on tools and resources that deliver actionable insights. For example, a SDMM may help an organization reduce the number of ineffective or overlapping security tools.
Aligning to the Security Data Maturity Model provides and can be vital to helping democratize data across organizations, enabling large and small teams to make better data-driven decisions for security, governance and compliance.
The five stages of the Security Data Maturity Model
Comcast’s own cybersecurity team spent years building a security data fabric to better operationalize and optimize security data to help improve threat responses and cybersecurity oversight. In the process, they created the SDMM and identified five stages, mapped from less mature to more mature. Greater maturity implies greater strategic value and efficacy to the organization.
The stages are described at a high level below and consist of Aware, Reactive, Informed, Enabled and Prescriptive.
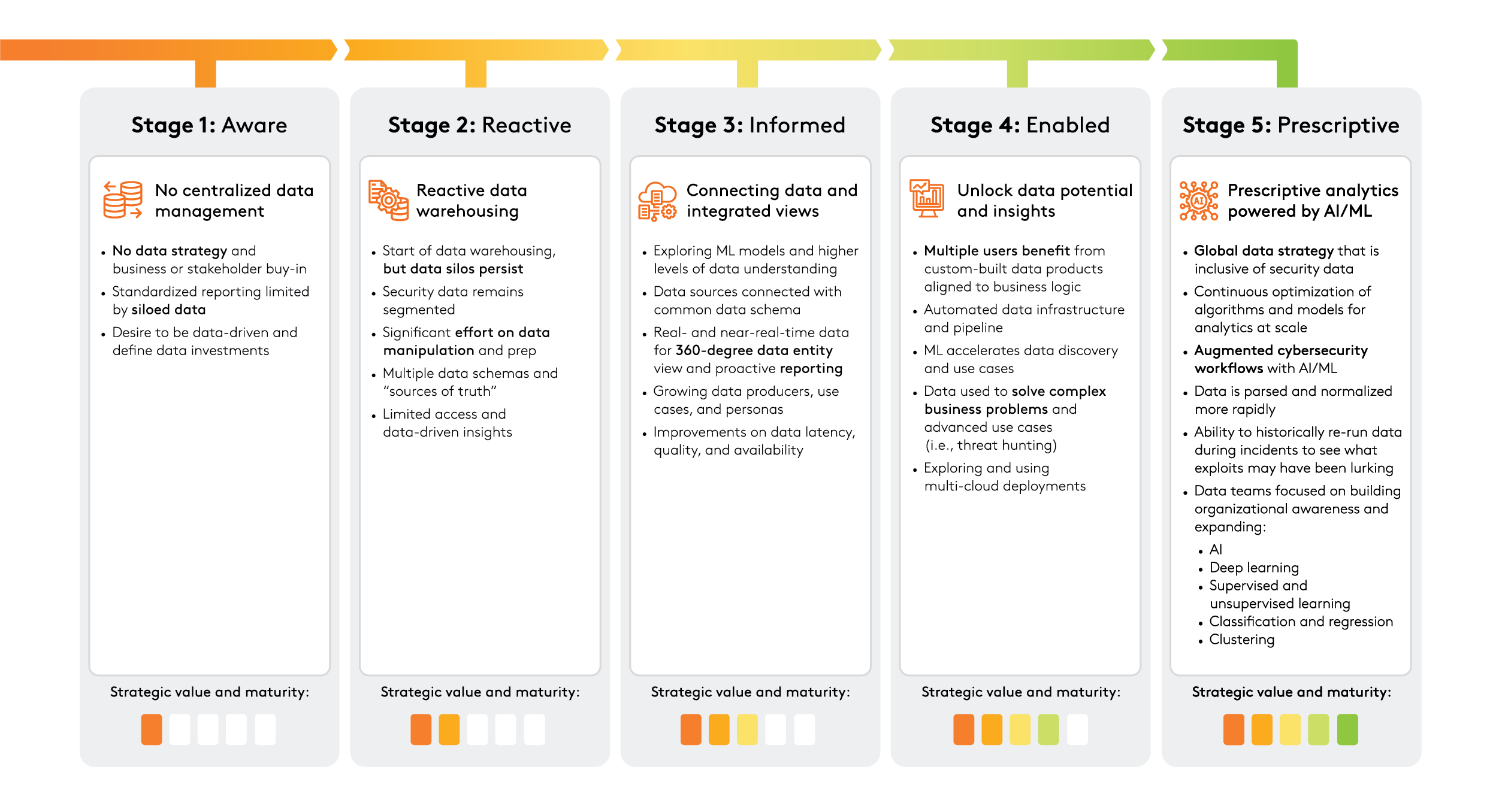
Understanding where your organization lies within the SDMM can help determine the resources and investment required to move to the next maturity level.
As an organization increases its security data maturity, the core topic becomes less about what type of data is stored or what type of threat hunting is effective and more about benefiting from prescriptive analytics using AI and ML. The strategic value of an organization’s data moves in parallel with its data maturity.


