“Compliance” is a word that can cause people to wrinkle their noses involuntarily. It’s associated with time-consuming, mundane, repetitive tasks whose only purpose is to check boxes off a list. Nothing could be further from the truth. Compliance is crucial to the cyber health of a modern data-driven organization. Older ideas of compliance as a minimum set of requirements and a necessary cost center are dying out as the implementation of better technologies transform it from a business burden into a revenue enabler.
When organizations shift their mindset, they can leverage their compliance posture to build revenue-generating customer trust. In the cybersecurity and data privacy realm, compliance offers objective third-party assurance over the effectiveness of an organization’s risk mitigation controls. Whether a business caters to commercial or consumer customers, it can use this validation to reduce the time to purchase and build confidence.
Organizations can view their Governance, Risk, and Compliance (GRC) programs as business enablers by understanding compliance and how to build an efficient compliance program.
What is compliance?
Compliance consists of the internal policies, processes, and activities a company implements and maintains to ensure it follows externally defined rules. Compliance management is the monitoring an organization does to ensure that workforce members follow the internally designed policies, procedures, rules, and behavioral standards.
External compliance requirements arise from:
- Laws: enacted by legislative bodies, like the US Congress or the European Parliament
- Regulations: implemented by regulatory agencies to whom a legislative body has delegated authority, like the National Institute of Standards and Technology (NIST) or a European Union (EU) Member State's Data Protection Authority (DPA)
- Frameworks and standards: defined by industry-focused organizations, like the International Organization for Standardization (ISO) or the Association of International Certified Professional Accountants (AICPA)
Meanwhile, corporate compliance consists of the internal rules that the company implements in response to these externally defined requirements.
What are some essential cybersecurity and data privacy compliance mandates?
As threat actors increasingly target the vast amounts of sensitive data corporations collect, store, transmit, and process, authorities publish new mandates. While staying updated on all new cybersecurity and data privacy requirements quickly becomes overwhelming, organizational leaders should be familiar with some key laws, regulations, and frameworks.
Laws
Multinational corporations must manage various legal requirements across various jurisdictions. Since violating laws can lead to fines or jail time, executives should be aware of the ones that impact their business operations the most.
Some mission-critical cybersecurity and data privacy laws include:
- EU General Data Protection Regulation (GDPR): establishes extra-territorial jurisdiction and provides data subjects with rights to consent to share data, request copies of data, correct data with mistakes, and delete data in the company’s possessions
- Health Insurance Portability and Accountability Act (HIPAA)/Health Information Technology for Economic and Clinical Health Act (HITECH): require healthcare delivery organizations (HDOs) and their business associates to implement technical and administrative safeguards under the Privacy Rule, Security Rule, Breach Notification Rule, and Enforcement Rule
- Australian Privacy Act of 1988 (APA) Updated 2019: applies responsibilities to any Australian citizens, companies, or subsidiaries that own or operate an organization and using a “reasonable person” standard to define data at risk
- California Consumer Privacy Act (CCPA)/California Privacy Rights Act (CPRA): establishes extra-territorial jurisdiction by granting all California consumers rights to consent, request, correction, and deletion and giving them the right to sue in civil court for damages arising from data breaches
- German IT Security Act 2.0: Establishes binding minimum security standards for detection, defense, and monitoring, as well as high-level security requirements for mobile networks
Regulations
Laws often delegate responsibility for enforcement to regulatory agencies because they know their industries better than the legislative body.
Some mission-critical regulations include:
- New York Department of Financial Services (NYDFS) Cybersecurity Regulation (23 NYCRR 500): formalizes requirements across all financial institutions doing business in New York, including continuous risk monitoring, continuous assurance, enhanced vendor risk management, documented cybersecurity policy, and hiring a Chief Information Security Officer
- Cybersecurity Maturity Model Certification (CMMC): requires all organizations across the Defense Industrial Base (DIB) to achieve certification for their ability to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) before being awarded contracts by the Department of Defense (DoD)
- Payment Card Industry Data Security Standard (PCI DSS): identifies the administrative and technical requirements for any organization that collects payments online or via payment card reader, including fines and penalties for violations
Frameworks and industry standards
Frameworks and industry standards provide best practices for compliance with a law or regulatory agency mandate. Many laws and regulations cross-reference these frameworks and standards so that companies know how to map their controls appropriately. While organizations often use frameworks and standards to define the controls used to prove compliance, these do not apply fines or penalties for violations.
Some key frameworks and industry standards include:
- National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF): defines the five functions of a cybersecurity program as Identify, Protect, Detect, Respond, and Recover, then breaks them down into Categories and Subcategories to help organizations implement controls
- International Organizations for Standardization (ISO) 27000-series: establishes broad risk-based requirements and generalized guidance to help organizations develop an information security management system (ISMS)
- Center for Internet Security (CIS) Critical Security Controls: provides a maturity model containing eighteen control categories, with each incorporating various safeguards
Understanding compliance risk
Compliance risk is the potential material loss that could arise from violating a law, regulation, or industry standard. When organizations build their compliance programs, they typically consider the following risk types:
- Illegal practices: willful violations of law, like fraud or theft
- Human error: unintentional acts that lead to a compliance violation, such as accidentally sending an email containing sensitive information to the wrong recipient
- Data breach: threat actors gaining unauthorized access to systems and networks, like during a ransomware attack
- Process failure: failure to follow procedure or deviation from defined procedure, such as an employee sharing a password
- Operational or business disruption: inability to use critical data, applications, or networks to engage in daily business activities that leads to lost revenue
Nonconformance to a compliance requirement can lead to:
- Administrative/civil fines and penalties: monetary punishment, often assessed as the greater of a minimum baseline or percentage of revenue
- Criminal penalties: monetary punishment or incarceration, often assessed as a range based on the party's willfulness or malicious intent when violating the requirement
- Certification revocation: agency or governing body no longer allowing the organization to attest to its conformance publicly
- Civil lawsuits: lawsuits filed by administrative agencies or breach victims, holding organizations and possibly executive officers liable for data breaches
- Limited market access: contracts with industry verticals require audits and certification, like Federal Civilian Executive Branch (FCEB) agencies requiring FedRAMP or Department of Defense (DoD) requiring Cybersecurity Maturity Model Certification (CCMC)
- Cyber liability insurance challenges: inability to obtain or increased premiums for cyber liability insurance arising from lack of basic cyber hygiene controls
Who are the stakeholders responsible for compliance?
Compliance risk management requires various cross-functional stakeholders to collaborate. At the enterprise level, compliance has become more than a “check the box” process. Organizations find that governments and customers increasingly use it for assurance over cybersecurity and privacy programs. The documentation and third-party assessments provide transparency into a company’s policies and practices, a fundamental requirement for building trust.
Business Units, Departments, and Divisions
As the people working with their staff to handle daily compliance activities, line of business management acts as an organization’s first line of compliance defense. Compared to other internal stakeholders, this group is more technical and tactical. Their responsibilities include:
- Ensure that workforce members complete required training
- Track workforce members’ review of policies and processes related to their job functions
- Periodically review reports aligned to compliance objectives, like engaging in access reviews
- Engage in due diligence and risk assessments when seeking to procure a new work-enabling technology
- Manage intentional and unintentional workforce member compliance violations
- Delegate the responsibility for building reports so that they can use the visualizations to tell data-driven stories
Compliance and Legal Departments
As the departments with specialized legal and regulatory skills, the compliance and legal departments play a crucial role in establishing and maintaining compliance frameworks and standards by working with staff and management to ensure that the company identifies, manages, and mitigates all compliance risks. As the person tasked with tracking updates to compliance requirements and aligning them to business activities, stakeholders view them as the subject matter expert on organizational controls as well as the legal, regulatory, and industry changes.
The compliance officer’s responsibilities include:
- Identifying and communicating all laws, regulations, and industry standards to which the company must adhere
- Implementing and maintaining policies and procedures that act as internal controls for compliance
- Communicating updates to compliance mandates
- Organizing workforce member compliance training aligned to job function
- Working with business units to set guidelines for responding to compliance violations
- Implementing disciplinary measures for nonconformance
- Working with auditors to address findings
- Monitoring and reviewing compliance programs to identify areas of improvement
Auditors
Internal Audit teams, along with external audit firms when necessary, ensuring independent evaluation and verification of compliance practices. Many companies employ both internal and external auditors. Internal auditors review a company’s compliance program to identify violations so that the organization can correct issues before an external auditor engages in review, often acting like tutors to check work and provide helpful feedback for improvement. External auditors are objective third-party assessors who review the company’s compliance program often as part of a mandatory legal or regulatory requirement, similar to teachers testing knowledge and identifying gaps. Auditors provide assurance over whether the organization’s system of internal checks and balances works as intended, meaning that they rely on accurate data provided by other stakeholders responsible for day-to-day activities.
Whether the auditor is internal, external, or a regulator sent by an agency, the responsibilities include:
- Planning the audit
- Determining the audit’s scope
- Reviewing previous audit reports for findings to ensure the organization addressed them
- Engaging in pre-examination interviews with executive leadership to identify changes to the IT environment
- Identifying and requesting the policies, procedures, and technical documentation to compare what the organization should be doing to what it does
- On-site testing to ensure controls work as intended, including reviewing physical safeguards, interviewing staff, and asking for demonstrations to evaluate configurations
- Meeting with executive leadership to discuss any findings before publishing the report
- Publishing an audit report that includes an executive summary, background, objectives, scope, methodology, findings, and recommendations
Executive Leadership and Board of Directors
Executive leadership oversees the organization’s overarching compliance and risk management program. As the teams managing the company’s business strategy, these leaders align compliance and business objectives to create an integrated risk management strategy. It’s critical for these stakeholders to understand their organization’s compliance programs, ensuring they are meeting their governance responsibility while enabling data-driven business decisions and resource allocation.
Their responsibilities include:
- Review and approving the risk assessment and risk management strategy
- Assess the compliance function’s structure and capabilities
- Allocate financial, staffing, and financial resources across the compliance, IT, and security functions
- Review and respond to internal and external audit report findings
- Complete training as required by compliance mandates
- Stay informed about new compliance mandates or changes to current ones that affect the organization’s business goals
- Report to shareholders about the financial impact that a security incident has on the organization
Why is compliance management challenging?
For global enterprises, compliance management creates unique challenges. In the case of Comcast, as a company providing critical infrastructure, threat actors continuously target our vast digital landscape, which includes thousands of employees and contractors, operations across multiple continents, and even amusement parks. Aggregating the data collected from our diverse and expansive cybersecurity technology stack into a comprehensive, optimized data lake is critical to achieving our compliance objectives.
Evolving threat landscape
Threat actors work to circumvent every new protection a company implements. As security researchers announce new vulnerabilities, attackers find ways to exploit them. Further, organizations struggle as sophisticated malicious actors deploy zero-day attacks by discovering and exploiting previously unknown vulnerabilities. As organizations add new technologies to mitigate these risks, they often lose visibility into whether their controls remain effective. The tools often lack a common data schema, preventing security analysts from seamlessly correlating events across these complex integrations.
Changing legal and regulatory landscape
Legislative bodies and regulatory agencies continue to implement new compliance requirements to hold organizations accountable for mitigating risks arising from new business models and attack methodologies. For multinational corporations, tracking these changes and staying compliant becomes overwhelming.
Expanded attack surface
Organizations adopting new cloud-based technologies increase the number of access points malicious actors can exploit during an attack. As companies respond to new threats with point solutions, they can expand their attack surface beyond the business technology environment. New cloud-connected technologies, both productivity and security enabling, add the number of potential attack vectors connected to IT environment. Security teams struggle to identify various vulnerabilities, like insecure Application Programming Interface (APIs) and stolen access credentials, inherent in these tools that undermine their cybersecurity and privacy controls.
Outdated mindsets
Historically, organizations viewed compliance as a point-in-time process comparing requirements to their activities and checking off boxes. Today, risk-based compliance mandates require organizations to continuously monitor, either explicitly or implicitly, for new risks with a goal of forcing them to respond to control drifts and new threats as quickly as possible.
5 Best Practices for Security and Privacy Compliance
Organizations should regularly test and monitor their controls to ensure they remain effective and compliant. However, to do this, they must move away from manual processes. Organizations collect vast quantities of security information, from syslogs to vendor-specific firewall logs to DNS records. Using automation that enables them to map controls across frameworks and operational regions enables them to engage in continuous controls monitoring (CCM) for continuous compliance assurance.
(1) Leverage a data lake to optimize data storage
Security and risk management teams collect data from across their IT and cybersecurity technology stacks. However, storing this data becomes expensive, meaning they often feel they must balance collection and cost.
By leveraging a data lake, they maintain control of their data while gaining the ability to contextualize it. For example, using a data lake to store their security telemetry means they can aggregate, correlate, and analyze data from technologies like:
- Endpoint detection and response (EDR)
- Intrusion Detection Systems (IDS)/Intrusion Prevention Systems (IPS)
- Identity Governance and Administration (IGA)/Identity and Access Management (IAM)
- Network scanners
- Configuration Management Databases (CMDBs)
- Servers
- Events logs and security logs
- Asset inventories
- Threat intelligence feeds
- Vulnerability Management and scanning
(2) Establish an aggregated and enriched repository of compliance data
Compliance relies on accurate data. Using a data lake enables organizations to aggregate everything, but they still need to parse and normalize that data to use it effectively. Further, they need a way to ensure data quality and integrity. By parsing, flattening, and auto-normalizing data within the data pipeline’s first steps, various compliance stakeholders can use it effectively and efficiently. With a single source of clean compliance data, all internal and external stakeholders have a shared understanding of and consistent insights into the controls’ effectiveness.
(3) Build KPIs based on organizational risk tolerance
Every cybersecurity and data privacy compliance mandate begins by requiring organizations to engage in a risk assessment to determine their risk tolerance. While building on a foundation of risk management creates flexibility, organizations often find that their compliance tools fail to accommodate their unique needs. Organizations can develop risk responses and key performance indicators (KPIs) based on their security portfolios and business needs by starting with a data lake. Since everyone has access to the same data, the security, compliance, and risk management teams can build dashboards focused on organization-specific criteria for actionable intelligence that improves the company’s compliance posture.
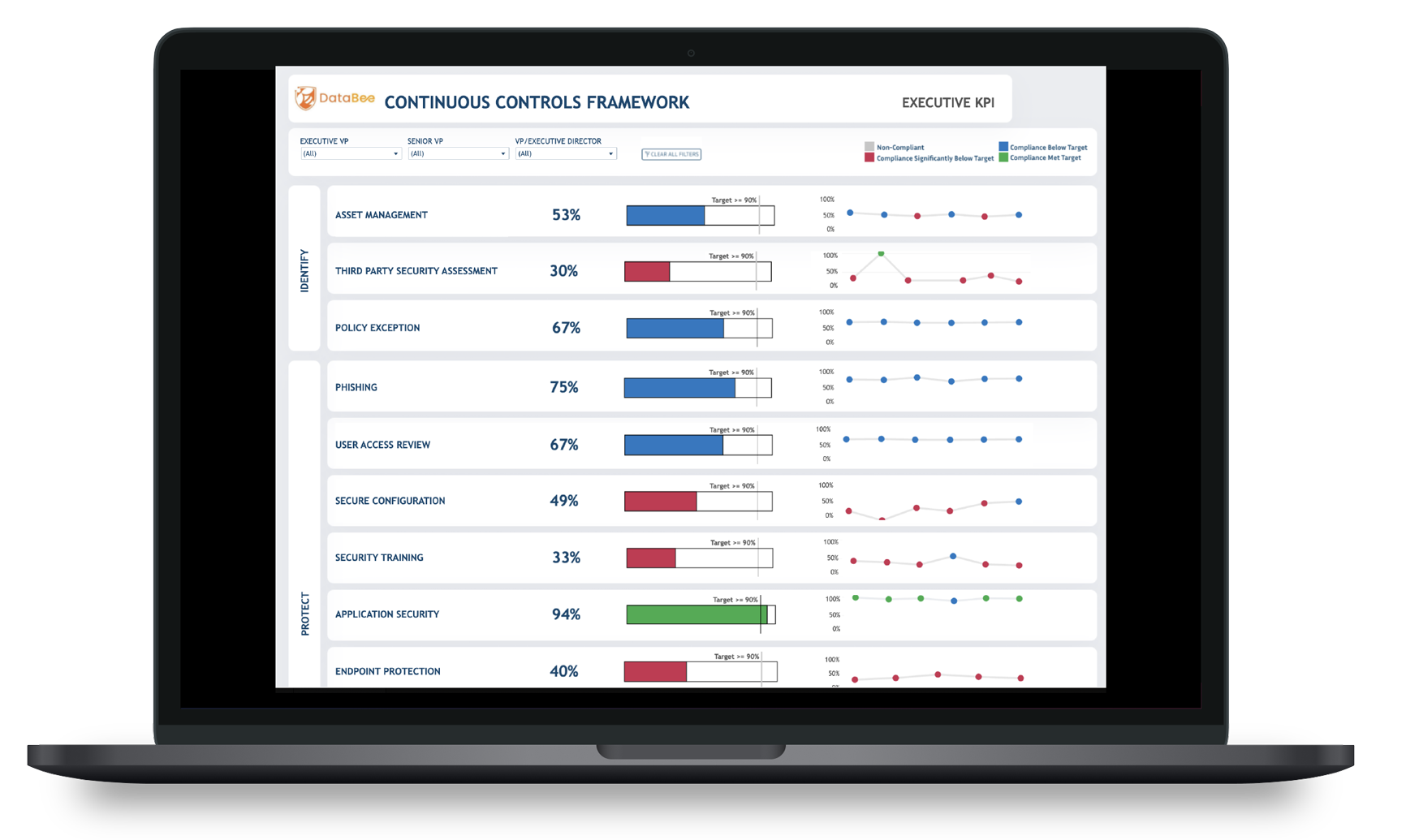
(4) Identify risk and prioritize remediation activities
With comprehensive cybersecurity and IT data visibility, GRC teams no longer need to worry about unexpected audit findings. They can weave together security data sources with asset owner details and organizational hierarchy information for a holistic view of the controls lifecycle. With continuously contextualized insights, they can more easily identify critical and at-risk resources, enabling them to make more informed recommendations about business strategy and future security technology investments.
(5) Operationalize reports to streamline audit reporting
Starting with a data lake enables organizations to provide the data that various stakeholders need in a format that makes sense to them. For example, executive leadership and boards of directors need visualizations that tie security metrics to business objectives. Meanwhile, security analysts need technical information that enables activities like patch management. Risk management teams can use the organization’s business intelligence tools to provide these reports, giving these strategic teams a way to prove governance over the compliance program.
Meanwhile, auditors need a combination of trend reports and technical evidence. Using a data lake, the people responsible for providing this documentation only need to go to a single source. This reduces the time and costs spent gathering audit documentation and responding to additional requests during the audit.