A modern, digitally transformed business collects vast quantities of data from employees, customers, and third-parties so that it can make informed decisions. Malicious actors, recognizing the data’s value, continuously evolve their attack methods to successfully exploit vulnerabilities across people’s skills, organizational processes, and new technologies. Organizations have struggled to keep pace with attackers as well as with legislative branches, agencies, and industry trade organizations that have doubled-down on data protection compliance mandates.
As governments pass more laws, and agencies establish more requirements, many senior leadership teams find themselves facing increased scrutiny. For example, the US Securities and Exchange Commission (SEC) filed “Wells Notices” that named SolarWinds’ CFO and CISO in connection with the company’s 2020 Cyber Incident. These Wells Notices indicate that the agency may bring an enforcement action against the company and its leadership in connection with its cybersecurity disclosures, public statements, internal controls, and procedures.
As federal agencies increasingly seek to hold individual senior leadership team members personally liable, compliance professionals have begun expressing concerns. According to survey results accompanying the 2022 National Society of Compliance Professionals Liability Framework, compliance professionals worry about being held personally liable with 66% of respondents concerned about liability arising from relying on inaccurate data from another employee.
For senior leadership teams and boards of directors, reliable data that integrates security, IT, and business context is critical to achieving their Governance, Risk, and Compliance (GRC) initiatives to protect their businesses and themselves from liability.
What is GRC?
Governance, Risk, and Compliance (GRC) is the set of policies, processes, and associated technologies that organizations use to align IT, privacy, and cybersecurity strategies to their business objectives. Organizations use GRC to assess the risks and benefits of adopting business-enabling and revenue-enhancing technologies. Then, the organizational leaders identify and implement the appropriate risk mitigation strategies that enable them to:
- Achieve business objectives, like increased efficiency
- Reduce uncertainty, like implementing processes and controls that respond to identified risks
- Gain and maintain compliance, such as implementing activities that respond to legislative or agency requirements
Governance
Governance is designing strategies that drive tactical risk management activities and engaging in oversight to measure the GRC program's success. An organization's senior leadership team and board of directors are responsible for ensuring that the organization has:
- Assigned responsible parties
- Analyzed risk
- Determined risk tolerance
- Established and implemented policies
- Reviewed metrics and reports
- Provided appropriate staffing and budgetary resources to maintain the GRC program
To fulfill their responsibilities, leaders need the data to help them make informed decisions. Some examples of this data include:
- Business impacts arising from a potential security or privacy incident, including business interruption costs and incident response costs
- Legal and compliance risks arising from a potential security or privacy incident
- Impacts that data protection controls and technologies may have on workforce members
Risk management
Risk management, as it applies to the data managed by the organization, is the process of analyzing and forecasting the potential business impacts that a data protection incident could have by:
- Identifying all sensitive data, devices, users, storage locations, and networks
- Analyzing the potential risk that all of these pose to the organization’s business
- Assessing the likelihood that a data protection incident will occur and the financial impact it could have
- Determining whether to accept, avoid, transfer, or mitigate the identified risk
- Establishing and implementing controls that reduce an identified event’s likelihood and proactively mitigate potential harms
- Monitoring to ensure that the controls remain effective even in a constantly evolving risk landscape
To adequately manage risk, organizational leaders and responsible parties need data such as:
- Organization charts to tie workforce members interacting with sensitive data to IT databases, like asset management tools to identify high-risk users, resources, and devices
- Financial impact that technologies have on the business to identify critical applications
- Third-party vendor lists to identify the ones that interact with sensitive data to implement enhanced monitoring
Compliance
Compliance is the set of policies, processes, and activities that ensure an organization follows externally and internally designed rules. Corporate compliance management strategies ensure that employees follow:
- External requirements defined by laws, agency regulations, and industry standards
- Internal rules implemented by company's policies and procedures that define how the organization will prove that it meets the external requirements
While compliance is often treated as a cost center, modern businesses increasingly need to prove to customers that data privacy programs are in place – and that they’re effective. An organization's compliance program enables it to:
- Provide customers assurance over its data protection initiatives
- Mitigate legal risk arising from lawsuits
- Reduce risks arising from fines for compliance violations
Compliance officers collect, share, and review documentation with internal and external stakeholders to ensure that the privacy and security controls remain effective. To adequately prove compliance, organizational leaders and responsible parties need data like:
- Technical documentation from IT, asset owners, and security teams that may include configurations, network maps, and identity and access management settings
- Business data, such as organizational charts, that document the organization's separation of duties controls or cyber awareness testing results demonstrating that employees have the appropriate training for their roles
- Trend data like vulnerability management and remediation activities, security incidents detected, or incident investigation times
Drivers for GRC
Any auditor or compliance officer knows how it feels to walk into a room and have people collectively sigh. Historically, GRC has been a time-consuming, annual, point-in-time, resource-intensive task. While it still takes a lot of time and energy, modern compliance can now be programmed to be a continuous, dynamic, process
As organizations adopt more cloud-native and Software-as-a-Service (SaaS) services, they increase their risk and attack surface. In response, it’s crucial to engage in governance, risk management, and compliance activities more purposefully and intentionally.
Achieve Compliance Objectives
Data protection has become a global legislative initiative over the past few years, and organizations need to implement programs that enable them to track their compliance posture. According to the United Nations (UN), out of its 194 member countries:
- 71% (137) have data privacy and protection laws
- 80% (156) have cybercrime laws
- 81% (158) have e-transaction laws
Further, the UN notes that of the 142 countries for which it could find data, 115 have adopted consumer protection legislation related to e-commerce.
Depending on the legislation, violations can lead to administrative fines or criminal sentences. Additionally, many consumer protection laws establish extra-territorial jurisdiction. For example, the General Data Protection Regulation (GDPR) applies to any business targeting European Union citizens no matter where they live. This means that companies selling to EU citizens living in North America or Asia still need to comply with the requirements. Many new consumer protection laws follow this extra-territorial jurisdiction model, like the California Consumer Privacy Act (CCPA) and the California Privacy Rights Act (CPRA). Further, several privacy-related bills have been brought before the US Congress over the last few years, indicating that a federal data privacy law is likely on the horizon.
Build Customer Trust
Whether an organization is a business-to-business (B2B) or business-to-consumer (B2C), their customers care about data protection. In the B2C market, the International Association of Privacy Professionals (IAPP) surveyed 5,000 consumers from 19 countries, finding:
- 80% are likely to stop doing business with companies that experience a cyberattack
- 68% are either somewhat or very concerned about privacy
- 35% ranked compliance with legal obligations as the biggest factor motivating companies to protect their privacy
For the B2B market, customers have a similar but different set of concerns. Many laws now incorporate “flow down” provisions, meaning that companies are responsible for managing their third-party vendor cybersecurity and privacy risks. Interconnected digital ecosystems means that vendors’ technologies often have access to an organization’s sensitive data. For example, a customer relationship management (CRM) tool will have customer names and email addresses, while an organization’s human resource management (HRM) solution processes employee and contractor names, addresses, and healthcare information.
Respondents to a report by Impritiva noted that:
- 51% had experienced a third-party data breach that resulted in direct or indirect misuse of sensitive or confidential data
- 44% experienced a third-party data breach or cyberattack directly or indirectly caused by a third-party vendor in the previous 12 months
To build strong, long-lasting customer relationships, companies need robust GRC programs so that they can allay fears.
Improve Cybersecurity and Privacy
Compliance is not security - any security or compliance expert will tell you that. Increasingly, organizations are moving towards a security-first approach to compliance, wherein they implement the security controls that mitigate identified risks, and then use compliance points as their internal set of checks and balances.
Companies take a security-first approach to compliance by first identifying risks, implementing controls, and monitoring their effectiveness. Then, they map the controls back to their chosen or required compliance mandate. During the mapping process, they may find gaps in their processes, giving them a way to iterate their programs and improve their overall security proficiency based on the internally determined risk profile and compliance requirements.
Increase Transparency
A comprehensive GRC program enables boards and directors to better fulfill their responsibilities to the organization. When senior leadership can communicate security proficiency and technical trends in business terms, directors can make informed strategic decisions. For example, when organizations have metrics proving their cybersecurity and privacy risk mitigations, directors can more precisely forecast revenue. Breaking down the data siloes between technical tools and business performance metrics, instills more confidence in the data organizations use for a more comprehensive, transparent decision-making process.
Reduce Infrastructure Complexity
As organizations scale their cloud strategies, new applications are incorporated that enable greater workforce productivity. As these efforts progress, they expand their attack surface since every new application creates a new access point that cybercriminals can exploit. These complex IT infrastructures incorporate new risks arising from:
- APIs
- External user access to resources, like contractors
- Internet of Things (IoT) devices, like printers or security cameras
- Data loss, like collaboration tools that have “share with a link” capabilities
In response to these increased risks, organizations adopt more cybersecurity technologies. According to the Palo Alto Network’s The State of Cloud-Native Security 2023 Report, today’s cybersecurity technology stack typically includes:
- 30+ tools for overall security
- 6-10 tools dedicated to cloud security
These estimates vary greatly with scale. Comcast NBCUniversal, for example, employs over 100 security tools. The complexities at this scale are compounded: each tool may have its own security data telemetry, making it difficult to bring data together into a common format to gain insights across the entire enterprise.
These challenges are not just relegated to the aggregation / normalization of metadata; they present additional hurdles for analysts striving to respond quickly, and compliance teams who need to report on the holistic effectiveness of the entire operation. From the same report, more than 75% of respondents reported that their organization struggles to identify which security tools can help them meet their needs.
Challenges with GRC
Despite recognizing the important role GRC plays, many organizations struggle to integrate it into their overarching business operations fully.
Inability to Update
Many organizations still maintain a “point-in-time” mentality, viewing GRC as a quarterly or annual activity. A rigid program fails to respond to changes in the organization’s IT environment or business strategies.
According to the PWC 2023 US Risk Perspectives Survey, risk professionals struggle to create a shared view of risk across the CEO, board of directors, and senior leadership team with:
- 9% included from the start across all major initiatives
- 40% not bringing risk insights to key stakeholders to shape decisions
- 51% not operating in a flexible way that facilitates collaboration across all three lines of defense
What are the three lines of defense?
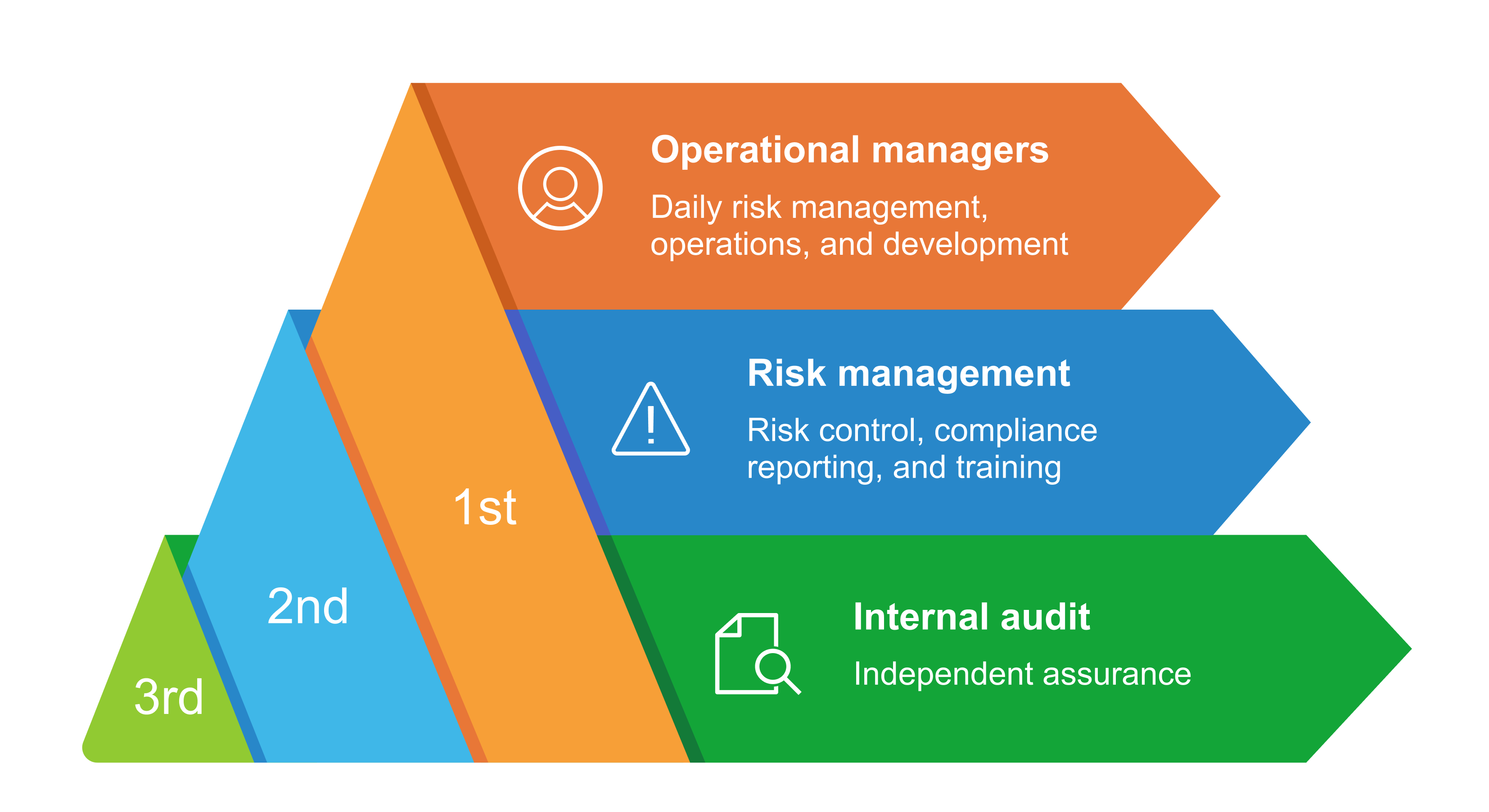
The three lines of defense model represents a framework for effective risk management within an organization. The first line of defense are operational managers, the second line consists of teams who are responsible for the risk management and compliance functions, and the third line is the internal audit process.
The need for a better, more integrated approach has never been greater. With reactive risk management still combined with legacy data silos, organizations lack a single, shared view of risk across CEO, board, and senior leadership team. This leaves them unduly challenged to establish common risk standards, and without a single, integrated data model to support their initiatives.
Inadequate Resources
Nearly every compliance mandate tasks senior leadership teams and boards of directors to provide adequate resources across IT, security, and compliance. To fulfill their responsibilities, funding must be approved for the staffing and technologies that support GRC initiatives.
Organizations implementing GRC solutions often need to consider costs beyond the technology, such as the staff needed to deploy, implement, and maintain the solution. When building budgets and hiring staff, considerations include:
- Software: perpetual licenses or subscription fees
- Implementation: staff to set up and deploy the solution
- Strategic consulting: experienced staff that understand GRC drivers and challenges to help determine the analytics models used to determine risk quantification
- Maintenance: Staff to enable training, support, and typical IT maintenance needs
When organizations fail to mature their GRC programs in tandem with scaling business operations, overall compliance costs can increase across departments beyond their compliance function.
High Operational Costs
Budgeting challenges can be encountered by even the largest enterprise organizations. Direct operational costs can include any or all of the following:
- Documentation: maintaining the risk assessment and controls, updating databases in response to IT environment changes
- Planning: scheduling assessment, planning audits, sending follow-up messages
- Evaluation: continuously reviewing risks and controls, mitigating and remediating issues, performing audits, reviewing incident response reports
- Monitoring: continuously testing and reporting on controls’ effectiveness, acting on recommendations, reviewing action plans and remediation activities
- Reporting: consolidating data, alerting stakeholders, triggering corrective actions in response to control ineffectiveness or anomalies
For many organizations, justifying a dedicated GRC solution is a challenge when they continue to implement the various, often-overlapping technologies that provide the security data that informs these activities. By primarily focusing on the security technology investments instead of the entire security structure, operational costs can be needlessly inflated by manual processes that could have been automated and streamlined.
Poor Data Management
As described earlier, enterprises with extensive scale may have a multitude of security tools. As cybersecurity technology stacks are built out over time, point solutions may have been adopted that just don’t integrate efficiently (or at all) with other tools. Further, each tool often has its own data schema, limiting the organization’s ability to correlate and analyze data effectively. Beyond the challenges that security analysts face when trying to respond to an incident, this makes reporting on cybersecurity program efficiency challenging and time-consuming.
Expanding the cybersecurity technology stack creates two distinct data management problems:
- Data silos: inability to aggregate and correlate security data arising from technological or functional limitations, like lack of APIs or reviewing textual data like processes or training documents
- Data quality: data duplication arising from overlapping security technologies undermining analytics models and trust between stakeholders
When security data remains siloed within the individual tools, organizations lack the ability to democratize its use. Giving all internal and external stakeholders access to the security tools undermines the principle of least privilege. For example, the IT department and a line of business vice president need to collaborate effectively and work from the same user access and device inventory data. However, providing the same level of access to the tools that manage these functions can expand the attack surface.
While GRC professionals seek to quantify risk, the technologies still leave gaps. The PWC 2023 US Risk Perspectives Survey found that:
- 57% of respondents use tech investment to improve their decision-making based on risk insights
- 56% of respondents said using advanced analytics have improved their ability to manage risks
- 85% of respondents cited improved quality as the most significant outcome of their data investments
Fundamentally, analytics models can only provide value when they can rely on the underlying data. Often, GRC tools ingest and analyze all security telemetry, meaning that they fail to deduplicate the data or compare data from disparate tools. These data issues leave teams struggling to identify overlapping information or analyze whether data provided from a single solution is a false positive. Manipulating this data to transform it into useful security intelligence becomes time-consuming and cost-inefficient. Without a single-source of deduplicated security data, GRC teams will remain unable to optimize their technology investments.
No standardized GRC Framework
Without the ability to appropriately report and collaborate across all key stakeholders, many organizations lack the structured approach to GRC that aligns with their short- and long-term visions. Many organizations turn to laws or regulatory agency publications to guide their GRC activities. These “best practices” outline steps that companies can take. They fail to provide directions about how to implement and measure the outcomes.
GRC frameworks are built on a foundation of risk to make them widely applicable regardless of an organization’s size or industry vertical. This flexibility creates its own unique challenges at the organizational and enterprise level, often arising from a lack of:
- Standardized metrics: lack of consistent measures for analyzing or expressing risk across digital assets and their associated systems
- Standardized risk scoring methodology: inputs for likelihood and impact calculations often rely on stakeholders’ personal experience or their industry’s typical practices
- Organizational or enterprise-level risk reporting: lack of mechanism for consolidating system-level cybersecurity risk data then mapping it to associated business processes
- Visibility: inability to identify, track, and manage risks that can cascade across the system, organization, and enterprise levels
Unclear Communication
The disconnect between system-level digital risks and overarching enterprise risk drives a larger challenge. GRC requires communication across various internal and external stakeholders; however, many organizations lack a single, consolidated source of all risk information because the needed data insights remain siloed under IT and security teams.
These silos mean that organizations cannot effectively:
- Normalize risk: consistent definitions and values across all stakeholders
- Aggregate risks: combine all risks into similar categories for a concise review
Without the ability to aggregate and normalize data protection risk data, organizations have impaired visibility into how data protection risks flow across:
- System level
- Line of business or department level
- Organizational
- Enterprise
Mature GRC with Data Analytics for Continuous Controls Monitoring (CCM)
Gartner defines continuous controls monitoring (CCM) as: a set of technologies to reduce business losses through continuous monitoring and reducing the cost of audits through continuous auditing of the controls in financial and other transactional applications.
CCM enables organizations to automate the control-testing process by incorporating near-real-time data. CCM platforms streamline many technical control monitoring and audit preparation processes like:
- Collecting, normalizing, and correlating control performance data for reporting performance
- Comparing control baselines to implementation outcomes
- Documenting adherence to security controls, policies, and procedures
- Continuously assessing and monitoring cyber risk in an evolving threat landscape
- Improving security incident detection, investigation and response
- Reducing the time and staff needed to gather audit documentation
- Identifying new or unmanaged assets
- Supporting the secure software development process
- Correlating threat intelligence with security data
While CCMs provide the technical control monitoring, they often lack the ability to ingest business-level data – meaning that they can continue to miss important risk identification, assessment, and management capabilities.
When organizations can implement a CCM that integrates business-level information, they can create a comprehensive, single source of data that allows all stakeholders to understand their current posture and future needs.
Manage Complexity with a Data Lake
When organizations leverage the power and cost-efficiency of data lakes, they can aggregate the vast amounts of collected security telemetry in a single location for a data-driven approach to continuous controls monitoring. With IT infrastructures that can generate hundreds of terabytes of data per day, most enterprises carefully select the event information forwarded to their Security Information and Event Management (SIEM) tool.
By storing security data and security telemetry in a data lake, organizations can optimize costs and enhance controls monitoring outcomes. With all security data in a single location, cleaned and normalized for form, organizations can minimize gaps in technical control and compliance. SIEMs need optimized data so security teams can build high-fidelity detection rules so the ability to leverage clean data stored in a data lake reduces storage costs and optimizes the SIEM deployment. By integrating a data lake into the data and SIEM infrastructure, organizations can store processed and raw data for both enhanced compliance with data retention requirements and improved analysis after an event.
Aggregating security telemetry in a data lake enables organizations to:
- Monitor activity across complex environments more precisely
- Reduce blindspots by providing access to all security data on demand
- Enhance event correlation for more visibility into controls’ effectiveness
- Improve analytics’ models with expanded datasets
Identify a GRC Framework for Compliance Mapping
Global enterprises must achieve compliance with various data protection laws, regulations, and industry frameworks. To reduce the operational costs arising from this complex compliance landscape, the chosen GRC framework must be flexible and internationally recognized so the organization can establish standardized policies, processes, procedures, and metrics across these diverse mandates.
For example, the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) provides a strong foundation for a data protection compliance program as well as guidance for reducing cybersecurity risks. NIST CSF breaks data protection activities into five primary functions. The Functions are organized into Categories and Subcategories of primary cybersecurity outcomes to help an organization better manage its cybersecurity efforts. The Framework does not define how to achieve the outcomes. Instead, it cites “Informative References,” such as NIST 800-53, that provide specifics for practices and controls to achieve the outcomes.
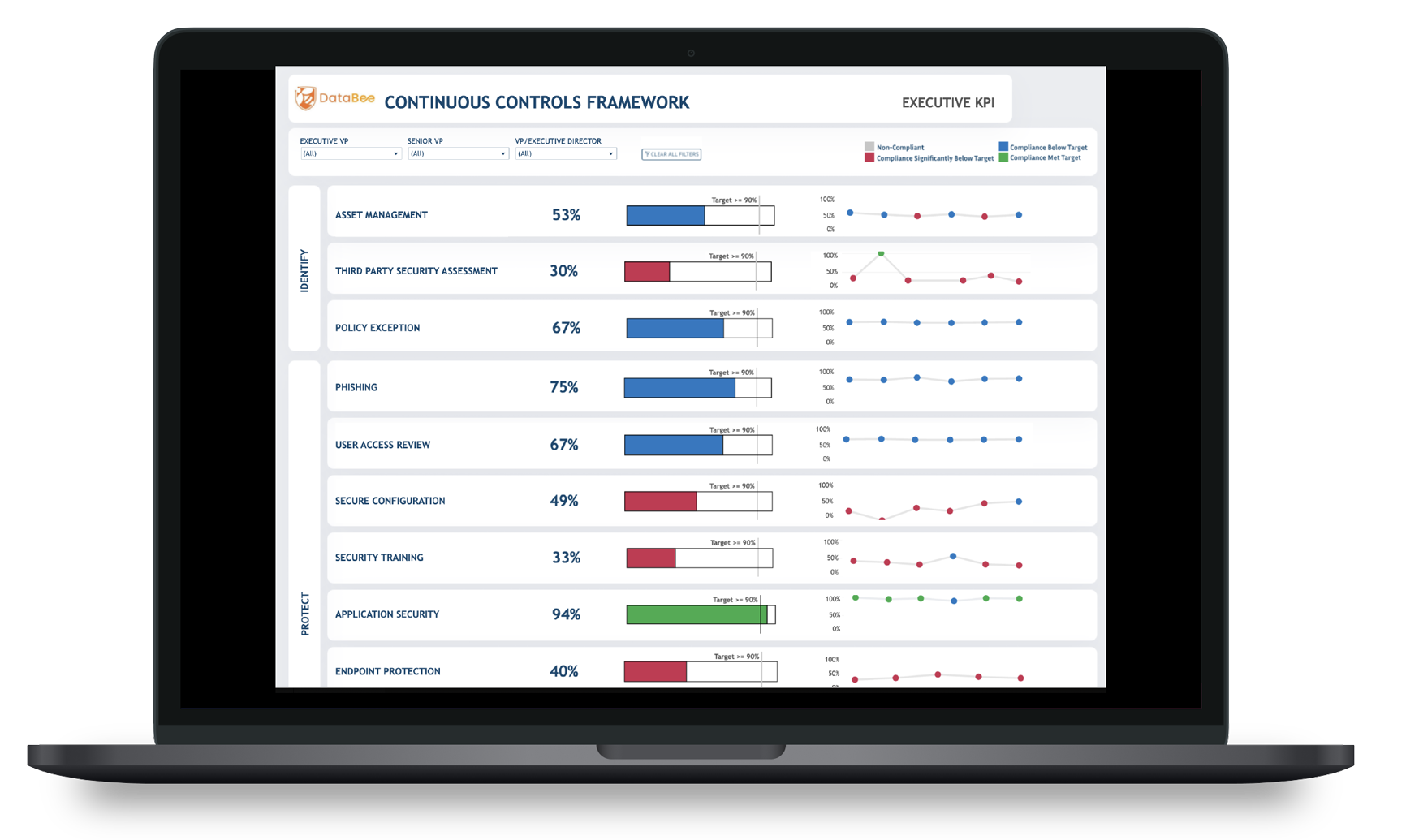
Enhance Governance by Integrating Technology and Business Data
Accountability is the cornerstone of governance. Using a data lake containing normalized security data, organizations can more easily connect and access previously siloed information.
For example, at the enterprise level, the CISO needs visibility into the percentage of devices covered by the company’s endpoint security solution.
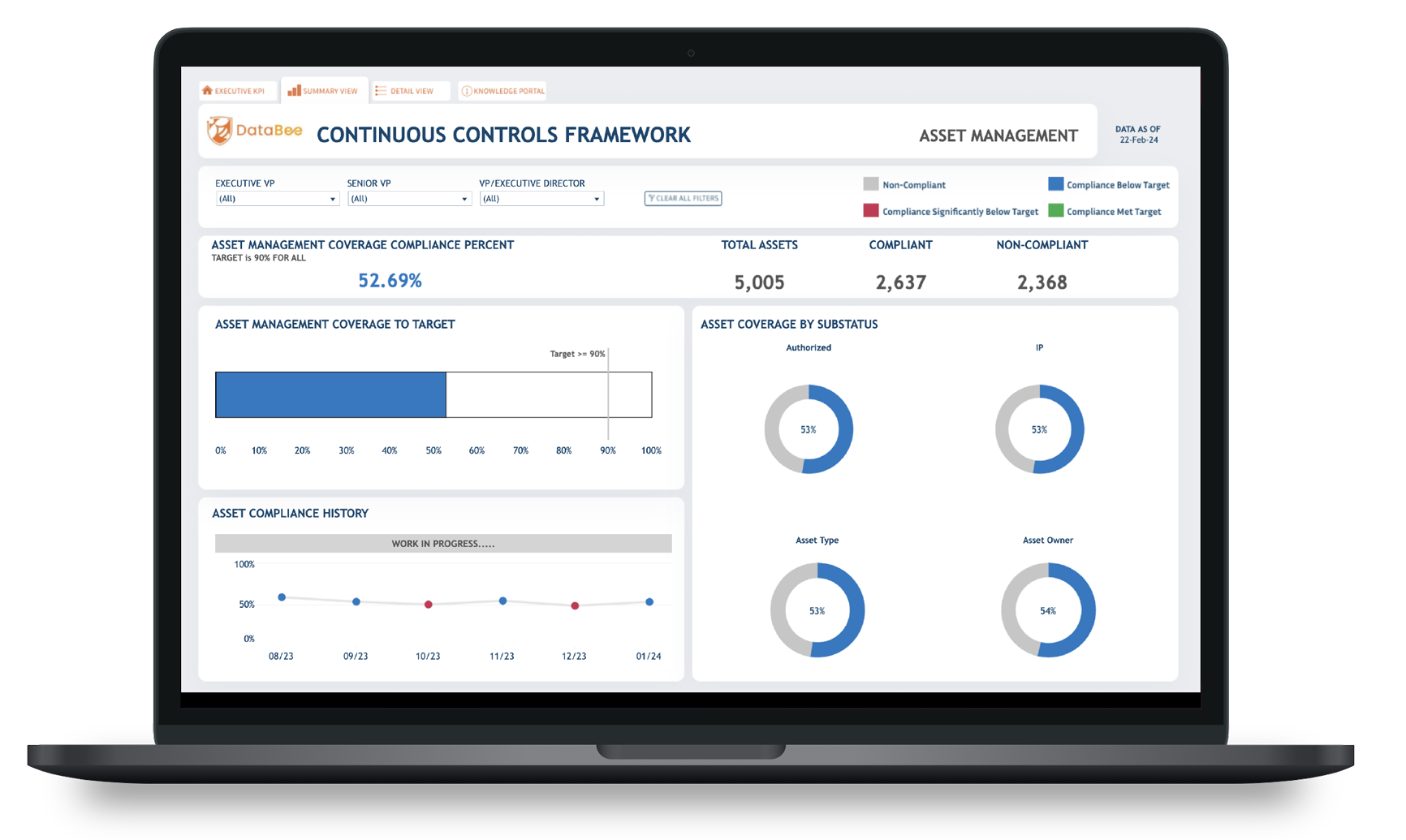
If the CISO identifies a compliance violation, then they need to identify the responsible party which can be a time-consuming process that requires cross-referencing various technologies like:
- Endpoint detection and response (EDR): Identifying the non-compliant device
- Asset inventory: Linking non-compliant device to corporate device owner
- Identity and Access Management (IAM): Linking device owner to job function
- Human Resources Data: Linking user job function to department and manager
A security solution that aggregates, normalizes, and correlates security data in a data lake provides one-click visibility by weaving together:
- Security data sources
- Asset owner details
- Organizational hierarchy data
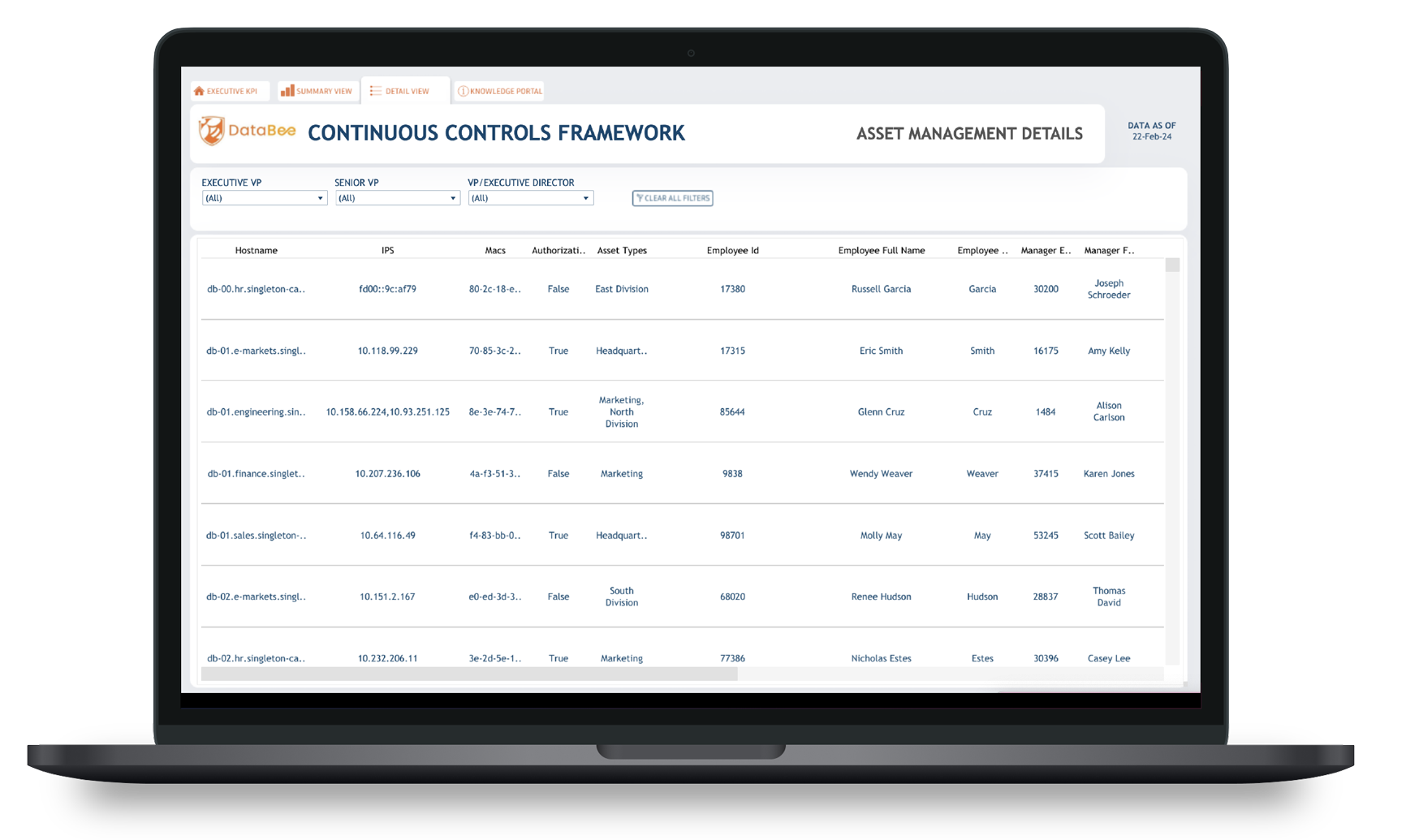
With the right security solution, the organization simultaneously
- Enhances governance through increased organizational visibility
- Reduces administrative costs arising from time-consuming investigations
Customize KPIs for More Precise Program Evaluation
Governance includes control over and visibility into the key performance indicators (KPIs) measuring the effectiveness of data protection controls. As an organization matures its technical controls, it must iterate the KPIs used to measure program success. When organizations use traditional governance council (GC) products, they must rely on the data that the tool ingests and the analytics the vendor supplies. Over time, these generic data points no longer provide adequate evaluation because the organization lacks control over how the analytics use the data sources.
When an organization defines the data sources and values, it gains control over how it evaluates program success. By leveraging the power of analytics, the enterprise can customize:
- Program targets across various objectives
- Data sources used to generate scores
- Update frequency to align with risk tolerance
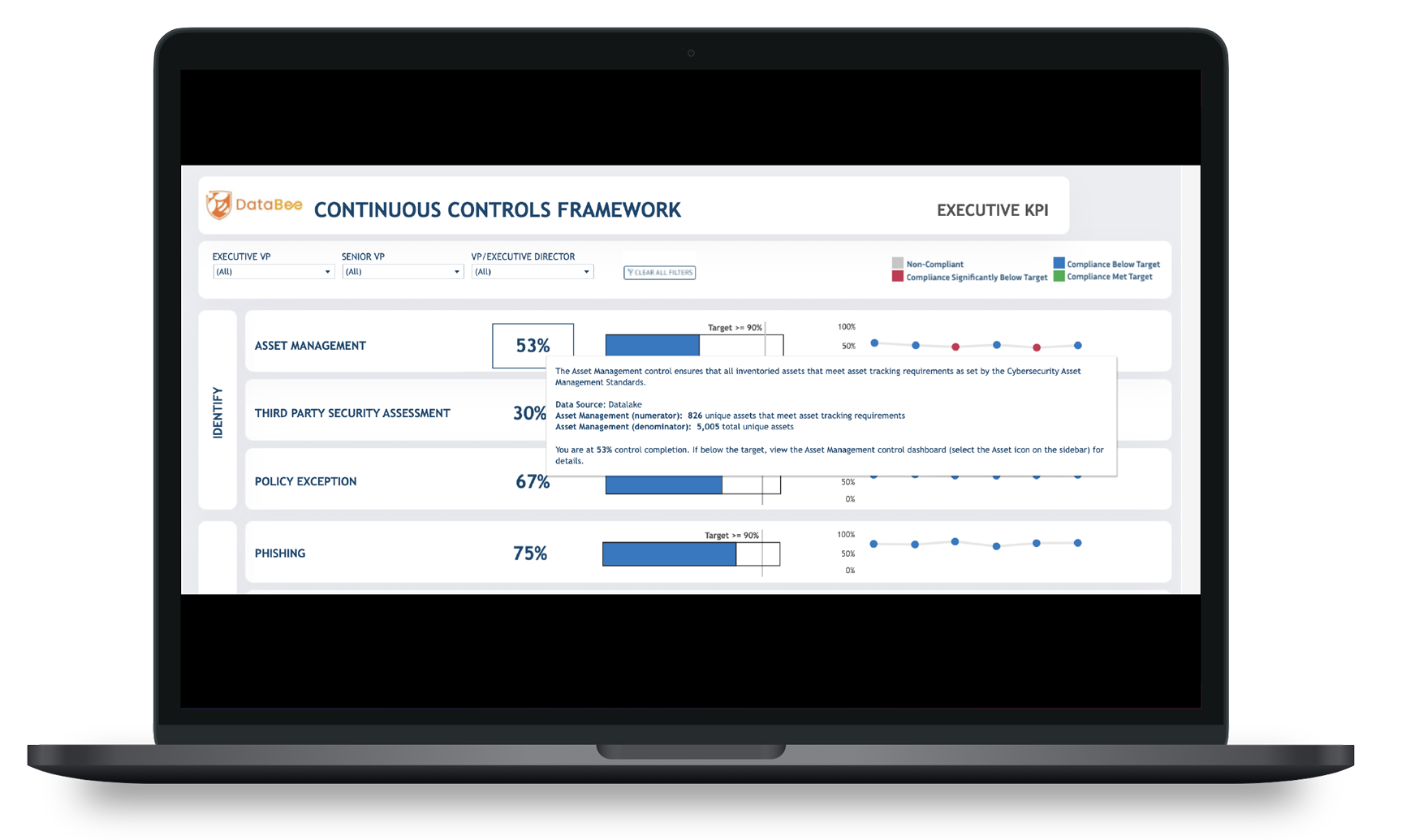
With this visibility and control, the organization’s stakeholders enhance their ability to make data-driven decisions because risk and compliance program KPIs are no longer a black box of proprietary analytics.
Improve Collaboration with a Single Source for Documentation and Reporting
GRC is a team sport consisting of various internal and external stakeholders. To achieve desired data-driven compliance outcomes, everyone involved should work from the same data and metrics. Simultaneously, stakeholders need data presented in a way that makes sense to them within the context of their job functions.
By using a data lake to aggregate all security telemetry, organizations can leverage their existing business intelligence and visualization tools when reporting their compliance activities. With these visualizations, a CISO can communicate the following to senior leadership and the board of directors:
- Cybersecurity technology return on investment by connecting tools to other key data points
- Security tooling and staffing gaps based on the identified compliance gaps
- Additional workforce cybersecurity training by combining compliance gap data with responsible party data
Incorporate Cybersecurity into Enterprise Risk Analytics Models
With a solution that incorporates necessary ETL and cybersecurity data analytics, the organization’s data scientists can focus their attention on filling a critical GRC program gap, integrating cybersecurity risk management metrics into the overarching enterprise risk profile.
At the system level, the organization’s security tools provide visibility into how well the security controls mitigate risk. At the organizational and enterprise levels, security analytics and continuous controls monitoring ensure that stakeholders understand the effectiveness of the overarching data protection program.
For a robust enterprise risk management strategy, companies need analytics models that enable them to integrate:
- Regulatory risk
- Financial risk
- Data breach risk
With a cybersecurity data and analytics solution, the enterprise data scientist teams can focus their attention on eliminating this gap.



