Answer the ‘who’ and ‘what’ questions about your cyber assets
Don’t let a simple question set off a chain reaction of frantic searches just to understand an enterprise’s assets or devices, who owns them, and their purpose.
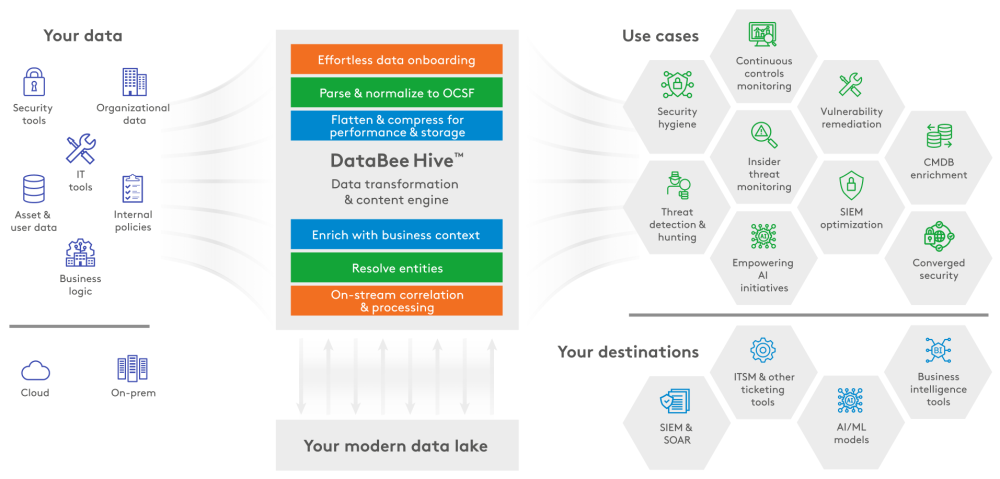
DataBee delivers cleaner and more complete user and asset information that is prioritized within the context of business and security. Leave manual entity correlation and processing in the past. Security and IT teams have information at their fingertips to enhance security coverage, increase alert accuracy, monitor compliance, and respond to incidents faster.
- Report on cyber and asset hygiene with context
- Enrich CMDB for a more accurate source of truth
- Monitor security controls and remediate vulnerabilities
- Bring together physical and information security insights
- Find and validate asset details with BeeKeeper AI™
DataBee helps you enhance your security posture by giving you visibility into your security and IT stack, helping you maintain the health and integrity of your systems, users, and data. Whether you’re assessing employee trainings or monitoring for software updates and patching, your team can visualize cyber and asset hygiene in BI tools like Power BI and Tableau.
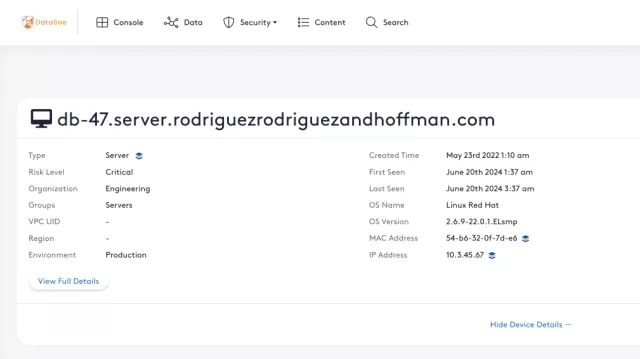
DataBee uncovers redundant tools, identifies potential misaligned asset or device owners, and suggests new owners for orphaned assets. By aggregating security and non-security logs like authentication logs and using entity resolution to reconcile asset information, DataBee can help you keep your configuration management database (CMDB) and other asset inventory systems more up-to-date, actionable and accurate.
DataBee helps reduce risks by providing continuous monitoring of security controls coverage and gaps. When paired with DataBee for Continuous Controls Monitoring (CCM), organizations can meet compliance requirements like EDR deployments with pre-built dashboards that measure and track deployment coverage and progress based on internal policy and organizational hierarchy and logic. DataBee can identify owners of vulnerable assets and enable quick remediation.
DataBee delivers converged security insights about a user by combining their physical and information security details. With physical information such as badging logs weaved in with human resource (HR) information and authentication logs, your security team has a more holistic and accurate timeline of a user’s activities, helping to identify malicious or negligent insider behaviors.
BeeKeeper AI from DataBee uses genAI capabilities to make asset validation an automated chat. Powered by a patent-pending entity resolution technology, DataBee makes prediction about asset ownership by analyzing who and how the asset is engaged. BeeKeeper AI connects to your organization’s chat client and reaches out to users to verify asset information and ownership.
Why Security Hygiene Matters
It’s the ultimate goal of cybersecurity and compliance: The ability to understand and index every user, every device, every asset in an organization’s digital environment. Better security hygiene means better answers to security questions.
Enterprises have an expansive asset and user population, so being able to identify unknown or traceable asset represents a potential entry point for bad actors, insider threats, and unintentional compliance violations.
Get a custom security hygiene demo
Transform your security and IT data points into integrated and accessible intelligence.