- Comprehensive user and activity profiles
- Discover deviations in behaviors
- Enhance security workflow responses
- Detect insider threats over the stream
Make manually correlating entity information a relic of the past with DataBee. Entity-centric views of a user or devices and their activities are created using entity resolution by aggregating information from multiple data sources, merging duplicate entries, and suggesting potential owners for devices and assets. Monitor users throughout the network even as IP addresses change over time and different logs refer to the same entity by different names.
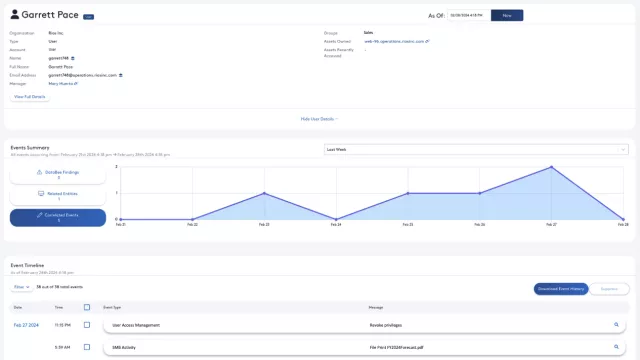
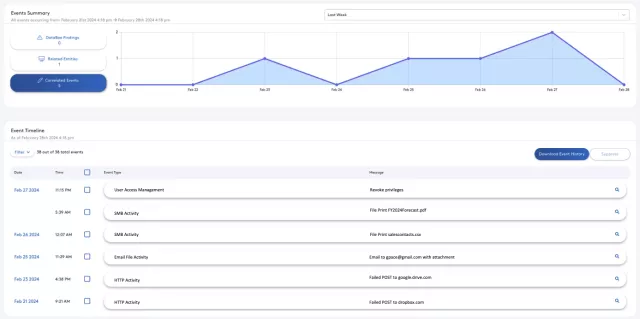
Get a bird’s-eye view of deviations from normal baselined patterns with Entity Views in the DataBee console. Gain an actionable chronological analysis with Entity Timelines, tracing when resources were accessed and the interaction between entities and applications. With DataBee, security analysts have “time awareness” and visibility into who, what, and when anomalous behaviors were detected in addition to comparing the current information of a user or device with any point earlier in the timeline.
DataBee assists in insider threat investigations with integrations to your security workflows. The enhanced security findings and context can be sent for security automation and to help improve anomaly detection models. Security and data engineers can use Jupyter Notebooks, Python, SQL, and other languages directly on the transformed security data to craft AI/ML models that learn from your data, adjusting baseline behaviors using your business context including organizational hierarchy, business line, level, location, and other information.
DataBee helps you sift through high-volume data sources, applying Active Detection Streams that send logs that trigger a potential insider threat alert for analysis. Additionally, with native Sigma rules support, DataBee lets you create correlation rules once without needing to update log parsers or vendor-specific security detection content.
Identify suspicious patterns
Garrett Pace's profile shows activities over the past week that, while seemingly routine, signal a more nefarious intent when correlated together.
Unify user & device visibility
When indicators of compromise or attacks are coming from inside the network, DataBee enables threat hunters to have a unified entity view of users and devices to uncover potentially malicious behaviors.