Tale as old as time
True as it can be
Barely even friends
Then somebody bends
Unexpectedly
Miscommunication and preconceived notions sit at the core of any frenemies to lovers story. It's a staple in storytelling — two people who initially clash become lovers who understand each other.
In the business world, governance, risk, and compliance (GRC) is seen as something that business, cybersecurity, and IT have to do under duress. The process is time-consuming and perceived as busywork, often taking each group away from their preferred or “more critical” tasks. Without help from other departments, however, the GRC teams lack the data and insights they need to keep the business compliant.
Unsurprisingly, these teams have a lot more in common than they realize — they all want to be seen as business enablers. And when given the right tools, these teams can work together to communicate and share data more effectively by breaking down barriers (and data silos).
Misconceptions and miscommunications
In the context of a rom-com, the two protagonists often enter the relationship with preconceived notions. In Jane Austen’s “Pride and Prejudice,” Lizzie and Mr. Darcy both assume from brief interactions that the other person is overwhelmingly arrogant or aloof. In fiction, these misconceptions and miscommunications can be humorous. However, in reality, they can get in the way of effective collaboration.
When thinking about the perspectives of your organization’s cast of “characters” or stakeholders, you can see how these different biases can become problematic.
Compliance stakeholders
On the compliance side, GRC teams, chief information security officers (CISOs), and business information security officers (BISOs) often struggle to align their objectives and initiatives with the technical teams. If your business were a movie, these stakeholders might say something like:
-
“IT and security teams don’t understand business objectives.”
-
“Senior leadership won’t understand the technical reasons for the risk.”
-
“Department managers rubber-stamp everything without really looking at it or caring about it.”
-
“I can’t trust the data these other teams are sharing with me.”
-
“Cybersecurity awareness training never seems to work.”
Business leaders
Like the other protagonist, business leaders can come in with their own set of preconceived notions. They are responsible for day-to-day activities like sales, marketing, or accounting. Already working on their long deliverables list, these business managers can feel like the compliance stakeholders are adding new tasks unrelated to their key performance metrics. In a movie, these stakeholders might be overheard saying:
-
“Roles and responsibilities are too confusing!”
-
“There’s no easy way to show GRC teams I’m compliant.”
-
“I don’t have clear guidance on how to become more compliant.”
-
“I don’t know the process owners, and I don’t know who to go to for help.”
Hijinks (or violations?) ensue
In a rom-com, these misconceptions often lead to humorous hijinks where the protagonists find themselves begrudgingly working together. If your internal stakeholders were fictional characters, the miscommunications could simply lead to sarcastic conversations or create plot elements.
Without the right technologies, the teams are collecting and using data, but it remains siloed, which only leads to inconsistencies that fuel their inability to work together. For example, these stakeholders each need similar data but presented in different ways that meet their needs:
-
Compliance stakeholders: accurate historical and technical data linked to users and devices
-
Business stakeholders: responsibility and ownership assignments that link to the people they manage
All internal parties need organizational hierarchy data and business logic, but these insights typically sit outside the tools that each stakeholder uses. Without access to accurate data and insights, the different stakeholders continue to speak different languages, leaving them unable to implement and maintain the basic cyber hygiene necessary for compliance and data protection. These misalignments can have costly security and compliance outcomes, like:
-
Data breaches and security incidents
-
Fines and penalties
-
Audit findings
-
Increased audit costs
Unexpected realization
In every story, the misaligned partners have an aha! moment where they finally see their commonalities and their views shift. In fiction, these usually arise from some plot twist or catalyst event. In business, it may be more subtle.
As the regulatory landscape evolves, miscommunication and misalignment become a recipe for compliance and security disaster as GRC teams, process owners, and business managers become frustrated. In business, no one wants the catalyst event that brings these teams together to be a data breach or compliance violation.
Diverse teams need to see that they share the same goal but view it through different lenses. For example, all stakeholders care about user access, but they need different insights:
-
GRC teams: data supporting controls that limit user access according to the principle of least privilege
-
Security analysts: meaningful alerts that provide real-time detections for insider threats, including credential-based attacks
-
Business managers: ensuring workforce members have enough access to resources to complete their job functions
Most compliance professionals feel an emotion that borders on excitement when they show off their spreadsheets filled with macros, pivot tables, and equations. However, spreadsheets aren’t security or compliance platforms. When organizations can collect and retain the necessary data, they can use analytics effectively, giving all stakeholders access to the data they need while reducing costs. With the right technologies, these stakeholders can collaborate, find their commonalities, and impact revenue by:
-
Reducing data breach costs with a security-first compliance program that mitigates risk to generate cost savings
-
Maintaining a robust compliance posture to mitigate compliance risks, like fines and penalties that undermine revenue objectives
-
Building customer trust through successful audits that accelerate sales pipelines and generate revenue
By leveraging security data lakes and analytics, organizations reduce data retention costs and break down the data silos so that the different internal stakeholders:
-
Find their commonalities.
-
Rely on accurate analytics.
-
Gain real-time, actionable insights.
Better together: Snowflake with DataBee for Continuous Controls Monitoring (CCM)

When compliance teams, process owners, and business managers collaborate and communicate effectively, they reduce audit costs and improve security outcomes. More importantly, they see each other as partners working toward a common business outcome rather than obstacles to meeting key performance indicators (KPIs).
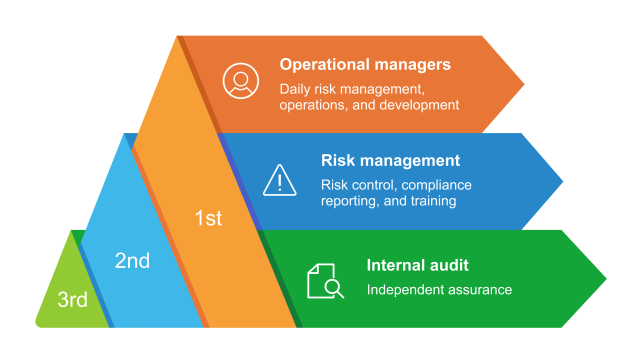
The best relationships are built on a foundation of shared experience where the partners support each other to overcome challenges. A CCM solution that puts data at the center can strengthen all three lines of defense, proving that teamwork really can make the dream work:
-
Operational managers: accountability with prescriptive guidance to reduce confusion and improve compliance
-
Risk management: fast, accurate reports driven by current data to eliminate point-in-time compliance and spreadsheets
-
Internal audit: focusing on higher-level tasks rather than searching for data or sending follow-up emails and requests
DataBee® from Comcast Technology Solutions brings your teams closer together because it brings them closer to your data. The security, risk, and compliance data fabric platform weaves together dissimilar security and IT data and enriches it with traditionally siloed business details — organizational hierarchy, for example — so that all users have access to actionable insights by creating:
-
A single source of truth: consistent, accurate, and continuous compliance reporting based on near-real-time data merged from multiple sources, like security tools, human resources’ databases, and asset management technologies
-
A single pane of glass: all three lines of defense viewing the same data at the same time for easier communication and reporting
With Snowflake, you get a platform that can support a wide range of architectural patterns, including:
-
Data lake: unlimited storage for versatile data types and workloads
-
Data lakehouse: transactional data lake for unified analytics, AI/ML, and collaborative workloads
-
Data mesh or fabric: distributed and governed, domain-oriented collaboration
When brought together with Snowflake, DataBee’s flexible and open architecture addresses your business needs today and allows you to adapt to changing needs in the future.
Learn more about DataBee and Snowflake
Join us on Wednesday, February 28, at 1 pm ET/10 am PT/18:00 GMT for “You, me, and continuous controls monitoring” with Yasmine Abdillahi, Executive Director for Cyber GRC at Comcast, and John Bland, Cybersecurity Data Cloud Principal at Snowflake, moderated by Tom Schneider, GRC Consultant for DataBee.

