All SIEMs Go: stitching together related alerts from multiple SIEMs
Today’s security information and event management (SIEMs) platforms do more than log collection and management. They are a critical tool used by security analysts and teams to run advanced security analytics and deliver unified threat detection and search capabilities.

A SIEM’s original purpose was to unify security monitoring in a single location. Security operation centers (SOCs) could then correlate event information to detect and investigate incidents faster. SIEMs often require specialized skills to fine-tune logs and events for correlation and analysis that is written in vendor-specific and proprietary query languages and schemas.
For some enterprises and agencies, it is not uncommon to see multiple SIEM deployments that help meet unique aspects of their cybersecurity needs and organizational requirements. Organizations often need to:
- federate alerts
- connect related alerts
- optimize their SIEM deployments
Managing multiple SIEMs can be a challenge even for the most well-funded and skilled security organizations.
The business case for multiple SIEMs
For a long time, SIEMs worked. However, cloud adoption and high-volume data sources like endpoint detection and response (EDR) tools threw traditional, on-premise SIEMs curveballs. Especially when considering the cost of ingestion-based pricing and on-premise SIEM storage.
While having one SIEM to rule them all (your security logs) is a nice-to-have, organizations often find themselves managing a multi-SIEM environment for various reasons, including:
- Augmenting an on-premises SIEM with Software-as-a-Service (SaaS) solutions to manage high-volume logs.
- Sharing a network infrastructure with a parent company managing its SIEM while needing visibility into subsidiaries managing their own.
- Acquiring companies through mergers and acquisitions (M&A) that have their own SIEMs.
- Storing log data’s personally identifiable information (PII) in a particular geographic region to comply with data sovereignty requirements.
Multiple SIEM aggregation with DataBee
Complexity can undermine security operations by causing missed alerts or security analyst alert fatigue. DataBee™ from Comcast Technology Solutions ingests various data sources, including directly from SaaS and on-premises SIEMs, stitching together related event context or alerts to help streamline the identification and correlation process. Alerts are enriched with additional logs and data sources, including business context and asset and user details. With a consistent and actionable timeline across SIEMs, organizations can optimize their investments and mature their security programs.
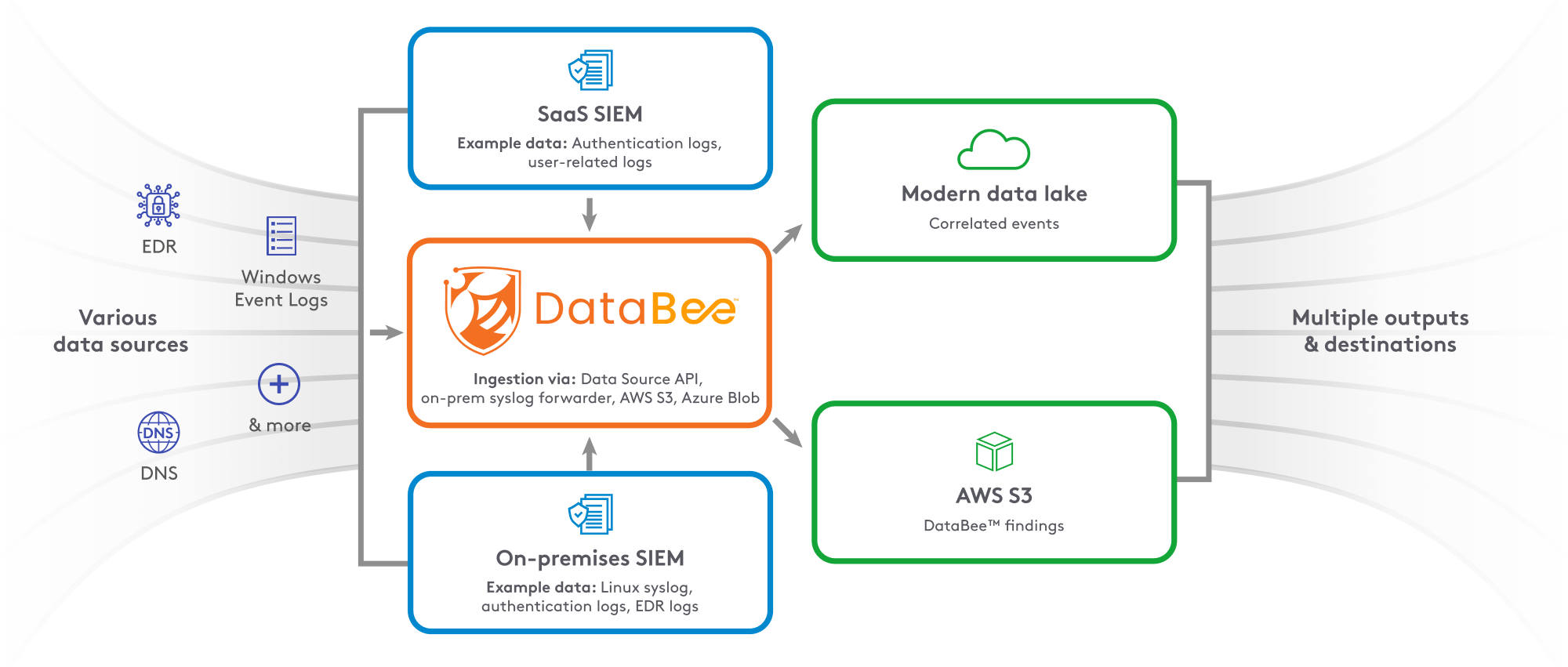
Normalization of data
An organization with SaaS and on-premises SIEM deployments may want to federate alerts and access to the data through the multiple SIEMs. This can be difficult to aggregate notable events during investigations.
DataBee can receive data from multiple sources including SaaS and on-premises SIEMs. DataBee normalizes the data and translates the original schema into an extended Open Cybersecurity Schema Framework (OCSF) format before sending it to the company’s chosen data repository, like a security data lake. By standardizing the various schemas across multiple SIEMs, organizations can better manage their detection engineering resources by writing rules once to cover multiple environments.
Enhanced visibility and accountability
With proprietary and patent-pending entity resolution technology, DataBee EntityViews ties together the various identifiers for entities, like users and devices, then uses a single identifier for enrichment into the data lake. With entity resolution, organizations can automatically correlate activity across numerous sources together and use that both in entity timelines as well as UEBA models.
Cost optimization for high-volume data sources
The adoption of cloud technologies and endpoint detection and response (EDR) have considerably impacted SIEM systems, creating a notable challenge due to the sheer volume of data generated. This surge in data stems from EDR's comprehensive coverage of sub-techniques, as outlined in the MITRE ATT&CK framework. While EDR solutions offer heightened visibility into endpoint activities, this influx of data overwhelms traditional SIEM architectures. This leads to performance degradation and the inability to effectively process and analyze events. However, leveraging the cost-effective storage solutions offered by data lakes presents a viable solution to this conundrum.
By utilizing data lakes, organizations can store vast amounts of EDR data at scale. This approach can not only alleviate the strain on SIEM systems. but also facilitate deeper analysis and correlation of security events. This empowers organizations to extract actionable insights and bolster their cyber defense strategies. Thus, integrating EDR with data lakes emerges as a promising paradigm for managing the deluge of security data while maximizing its utility in threat detection and response.
Real-Time detection streams
DataBee uses vendor-agnostic Sigma rules that allow organizations to get alerts for data, including forwarded data like DNS records. If the SOC team wants to receive alerts without having to store the data in the SIEM, the detections can be output into the data lake or any SIEM or security orchestration, automation, and response (SOAR) solution, including the original SIEM forwarding the data. By building correlated timelines across user activity between multiple SIEMs, organizations can gain flexibility across SIEM vendors so they can swap between them or trade them out, choosing the best technologies for their use cases rather than the ones that integrate better with current deployments.
Ready to bring together related alerts from multiple SIEMs? Let's talk!